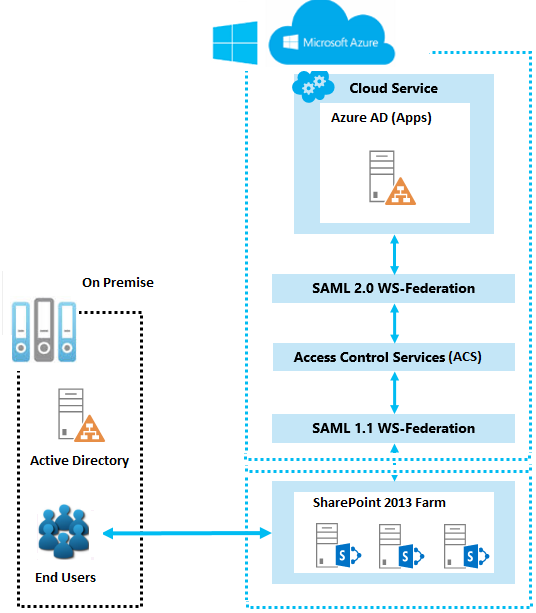
The below powershell script is to update a user profile property called 'CostCenter' and you can replace with your property and update it.
Add-Type -Path "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.dll"
Add-Type -Path "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.Runtime.dll"
Add-Type -Path "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.UserProfiles.dll"
$SiteUrl = "https://tenant-admin.sharepoint.com"
$password = Read-Host -Prompt "Enter password" -AsSecureString
$credentials = New-Object Microsoft.SharePoint.Client.SharePointOnlineCredentials("jollsam@tenant.com", $password)
#Set up the context
$Context = New-Object Microsoft.SharePoint.Client.ClientContext($SiteUrl)
$Context.Credentials = $credentials
$targetAccount = "i:0#.f|membership|jollsam@tenant.com"
$PropertyName= "CostCenter"
$Value = "17029"
$peopleManager = New-Object Microsoft.SharePoint.Client.UserProfiles.PeopleManager($Context)
Write-Host "Updating User Profile Property `"$PropertyName`" for account - `"$targetAccount`"" -ForegroundColor Green
$peopleManager.SetSingleValueProfileProperty($targetAccount, $PropertyName, $Value)
$Context.ExecuteQuery()
Add-Type -Path "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.dll"
Add-Type -Path "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.Runtime.dll"
Add-Type -Path "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.UserProfiles.dll"
$SiteUrl = "https://tenant-admin.sharepoint.com"
$password = Read-Host -Prompt "Enter password" -AsSecureString
$credentials = New-Object Microsoft.SharePoint.Client.SharePointOnlineCredentials("jollsam@tenant.com", $password)
#Set up the context
$Context = New-Object Microsoft.SharePoint.Client.ClientContext($SiteUrl)
$Context.Credentials = $credentials
$targetAccount = "i:0#.f|membership|jollsam@tenant.com"
$PropertyName= "CostCenter"
$Value = "17029"
$peopleManager = New-Object Microsoft.SharePoint.Client.UserProfiles.PeopleManager($Context)
Write-Host "Updating User Profile Property `"$PropertyName`" for account - `"$targetAccount`"" -ForegroundColor Green
$peopleManager.SetSingleValueProfileProperty($targetAccount, $PropertyName, $Value)
$Context.ExecuteQuery()